Well, it depends on your needs, and you should really start with a good discovery of what
SSSSHHHHHH LOUD WHITE NOISE
Look I’m going to do something that no one really wants to and lay it out straight. After that, we can get all excited and fight about it, but lets get this out of the way first:
If you have a large, complex, enterprise environment: Jamf Pro
If you are medium to large organization with a more simple structure: Mosyle Fuse
If you are a small business and just want to tweak a few things: Apple Business Essentials
There, that’s it. But what about Kandji, Jamf Now? AirWatch? InTune? Insert name of 500+ other MDM developers here?
You know, they all have their benefits. And if you have some compelling reason to use those instead of the ones I’ve outlined, by all means, use those.
But! You say! What about that advice you always give? You know… workflow your needs, chart out your strategy? So you don’t have a total failure on your hands?
Well, yes, you should still do that. Those are great things to do, and what’s more, you should pay me to do it! But the question wasn’t ‘What’s the correct process to avoid wasting a huge amount of time and money in IT?’ The question was ‘What’s the best?’ And there you have it.
So, lets get into the reasons why.
Scenario 1: You have a large, complex organization, or an existing complex IT infrastructure. Jamf Pro is going to do it all. Whatever it is you need to integrate with, whatever structure you have, Jamf is going to have you covered. Your security/data reporting/organizing/full MDM spec support is second to none, along with a passably decent graphical interface. Sure, 50% of those features boil down to ‘here’s a script the community made’ and while that is very annoying, the fact is, it works, and it speaks to the overall strength of the platform.
Of course, that same strength is exactly its weakness, which leads us to:
Scenario 2: You have a few, or even very many, devices you want to manage with the least amount of effort possible. Enter Mosyle, right through the wall, taking care of your problems like the baby of the Kool Aid Man and Arnie.
Mosyle just… does everything you would want it to do. Install and update third party apps that aren’t in VPP? Sure, done! Log in using Google or Microsoft logins? Sure, done! DNS filtering? Sure! Compliance scanning and remediation? Sure! (this last one is… huge. Extraordinarily huge, and, in some ways, a complete category buster).
Is the interface wonky and slow sometimes? Yeah. But can you pretty much figure it out without having to access the rather anemic documentation? Also yeah! And their support is pretty much flat out great. (Jamf Support is great too – once you’ve worked through five or six levels of appointments with people who do not, at all, understand your problem, that is. Still, at the top level, Jamf folks are the best in the industry, and they know it, we know it, and everyone else knows it.)
So, what’s left here?
Ah, yes:
Scenario 3: You don’t know what an MDM is, you don’t know why you’d want it, but you are annoyed that you can’t put the same apps on all the devices. Also, business storage, what’s that? But I do put all my stuff into an iCloud folder! Can my employees do that?
Don’t you worry, gentle, kind soul. Apple Business Essentials – or ABE, as it’s affectionally called by the deranged acronym producing community of nerds – has you covered. It will take care of basic management for your devices with the added bonus of having an interface you can absolutely figure out for yourself.
And there you go, that’s the upshot. One enables you to do do it all, the other does most of it for you, and the last one does a few things very easily.
All right. That’s what I claim. But how do we know that the other myriad – some very good, some very terrible – MDM’s aren’t as good? Well, feature wise, they may be, but this boils down to how you define ‘best.’ In our case, ‘best’ is short hand ‘the solution that most people will end up using due to a few key reasons.’ Mosyle is cheaper, Jamf has better community support and greater customization, and Apple Business Essentials, you know… just works. And that’s why, one way or another, a good 75 to 80% of clients who go through a discovery process end up with one of those products.
As always – ready for disclaimers? Here they come – this is deeply dependent on the very specific needs your IT environment may have. Already deeply invested in InTune and just want to manage some iPads? Well, stick with InTune. Want to set up a fully passwordless environment? Go with WorkspaceOne. Want to manage everything poorly and hate your life? Try on MaaS 360 or AirWatch!
Are you sharpening your keyboard right now with your love for Kandji? Jumpcloud? In general your hatred for one of the above?
Awesome. Look, the thing with questions like this is that if you already know some specific reason you love a product, you’ve gone through a discovery, (hopefully) know how your organization works, know what it needs down to specific details, and have picked something that will work for it best. But if you’ve done that, you aren’t googling questions like this. And if you are, I’m going to just be straight up and say you are likely going to end up with one of those three, and that’s okay.
But you should still do a discovery.
]]>
There have been a spate of news articles lately squabbling about whether or not Apple has lost its mojo. I was going to sit down and spout off about that in typical fashion, but instead I’ll show this little infographic.
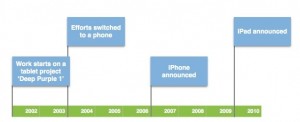
As you can see, there were five years between first beginning a new product line and bringing it to life. I’d make a pretty strong case that the iPad wasn’t a new product line but an evolution of the iPhone , as well as a return to the goal of the original project.
If we take these carefully arranged assumptions as true (watch my magic trick here), then we can go one step further and observe that at the time the iPhone was released, Apple was still a smaller company, R&D wise, than many and most likely could devote resources to one major new product at a time (I’ll back that up with observing that if development on a new project started in 2002 then that would be just a year after the iPod was released in 2001). Rolling along with that, that would mean that a new project would have gotten fired up around 2008 – 2010 (dependent on how much effort the iPad took). Which means we are in line for a new product sometime around this year which, let me check my notes, yep, they are promising.
But far more important is this: if I’m right (and I’ll bet you a donut I am) and new product lines were being developed shortly after the first iPhone, then señor Jobs was directly involved in those projects. Whatever the next few products are, people are forgetting that they will likely have been worked on for years beforehand.
This means we easily have one or two product cycles left before we actually start discovering what a Jobs-less Apple is like, one way or the other. That might not be the case if a horde of monkeys had magically taken over since Steve passed, but as we have all been made incessantly aware Apple is currently run by those who were most aligned with his vision. Further, even after these immediate new products, we’ll only get a chance to see the next round of new ideas another several years down the road.
So. I suggest we all take a big speculation chill pill when it comes to the future of Apple. Instead, we should speculate wildly about what is about to be released, because you know, rumors aren’t milling themselves.
]]>
History proves again and again that time marches on, but nothing ever changes, and those who fail to study history won’t be able to whip out boring historical facts at the drop of a hat. Or learn from it, I guess.
The story referenced above is exactly what people bandy about as ‘social engineering’ which is another way of saying ‘your fancy passwords don’t mean anything if GoDaddy tech support lets someone call and reset your password to something they request.’ As you no doubt already know, that is exactly what happened to the owner of the @N twitter account. With the godaddy account – and therefore domains, websites, and hosted information – in the invaders possession, he bargained with the owner of @N to turn it over the twitter account willingly.
There’s been a frenzy of online discussion (rightfully so) over this story. In terms of security advice, where do we go from here? Everything that’s been typically given as advice would have been thoroughly useless in this case. What advice do we give out now?
It’s fascinating to me that the refrain that’s gone up in many circles is ‘don’t store your credit card online!’. Really? It’s 2014 and we have to start having arguments again about the basic safety of online transactions, period, the way we were back in 1994? That’s a pretty dismal state of affairs.
A dismal state of affairs that is perfectly rational as long as your perspective is ‘prevent my account online being compromised at all costs’. Unfortunately, that’s an immediately problematic perspective, since that’s not really possible. The minute you hand over your financial or personal data to another entity, you surrender a degree of security that you simply can’t reclaim. The kicker is that it doesn’t matter if this is entity is online or not, all that matters is that it’s not you.
The most you can do is take reasonable steps to secure yourself, that will increase the balance of probability (thank you, mycroft) in favor of your information remaining safe. The trick lies in defining ‘reasonable’ . I would suggest ‘that which does not render useless the service you are attempting to use’. In other words, the same rule of thumb applies as with all things technological: when you start tipping the scales to something being a nuisance rather than a benefit in your life, it probably needs to go.
So is manually entering credit card information each time such a huge nuisance? In some settings, no. In settings where you are making multiple orders per day as part of a business? Where you don’t want to risk service interruption and have an auto-payment configured? In a life where we now have multiple online accounts for which we pay for things – for some even most things – on a daily basis on our phones? Um, yes. Can you imagine entering your credit card number on your AppleTV each time? Click, click, click goes the remote. Crash, it goes, out the window.
So what are we to do? Throw away the AppleTV? Give up on our credit card being safe and not use it? Well, you could do either, I suppose. But let me ask you this: do you assume that everything in your is completely secure from fraud?
Credit card companies already answered this a long time ago, and the answer is…. no. Fraud happens every ding dong day, and one of the excellent reasons to use credit cards, actually, is the protection they provide the user in insulating them from the cost of fraud. In fact, the kind of social engineering that the fraudster used to get access to the GoDaddy accounts in the above mentioned story is no different than the kind of fraud that plays out on the streets, supermarkets, and houses of the world every hour on the hour. We don’t stop commerce as a result, and we are hopefully not so naive to assume that there is no risk on a daily basis. We find ways to mitigate and soldier on.
If it helps, consider this: the number of cases where someone gains access in an illegal manner to your account via being a smooth talking swindler is exponentially lower than the number of people who outright have their credit card stolen. We don’t stop using credit cards as a result, and I don’t think we should stop using them in online accounts.
In other words, the entire semi-hysterical response to this event has been by people who have spent their life figuring out ways to prevent themselves of being victims online, and suddenly realized that when you give another company all your stuff, they get to make decisions about that stuff without consulting you, promises notwithstanding. Welcome to the cloud, everybody, it’s awesome, you have no control, enjoy.
Which, I believe, illustrates what the real lesson needs to be here: these companies need to get on the same bandwagon that Visa, MasterCard, et al, all got on a long time ago and flat out accept that fraud happens, preventing it entirely is impossible, and you have to have measures in place to repair the damange after it is done.
The real head-scratcher here is that Twitter has no way of looking at their records to see if it matches the story being told by Naoki Hiroshima, do some investigative work with both he and the current account holder and then give the account back if everything checks out. If they don’t have way to do that, they should , as should every other major internet services provider. And we should be demanding that they let us know that these measures are in place.
The other thing one should really do is backup all your website data locally, by the way.
]]>